As a device manufacturer, you aim for your devices to be both user-friendly and secure. For this, IT security must be considered already during product design.
With trust to automation in the IoT.
Using identities for your devices and IoT projects to meet IT security requirements and save 90% of configuration time.
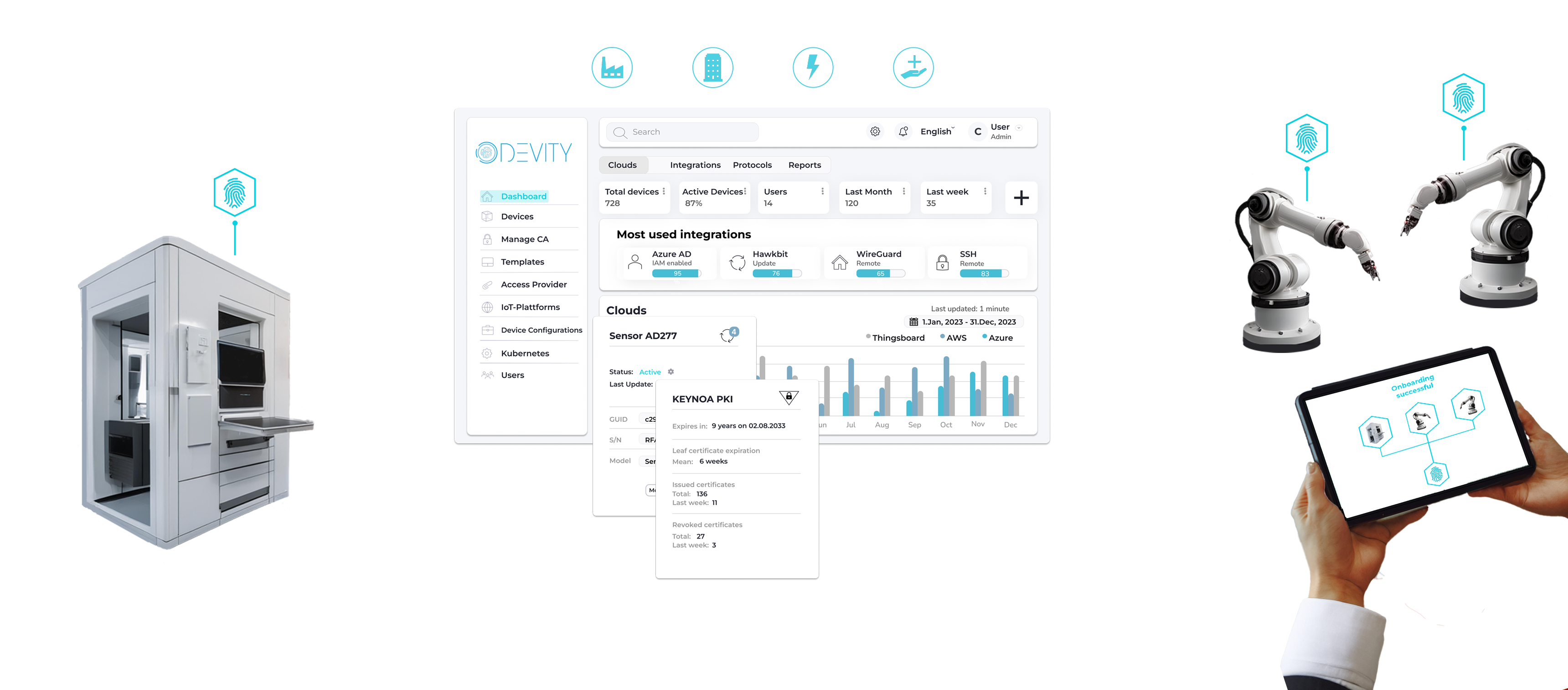
If you can’t trust the device, how can you trust the data?
Trust has never been more important or more complex than in a time with more devices, interactions, and regulations.
Do you meet the latest IT security requirements?
Standards such as IEC 62443, NIS-2 or the Cyber Resilience Act increase the technical requirements for protection against cyberattacks. Fulfill security-by-design without compromising on user-friendliness!
Are you using IT security for devices correctly?
92% of all industrial devices are configured insecurely.We help users of modern protocols such as MQTT and OPC UA securely authenticate devices and automatically maintain encrypted connections!
Are you ready for next-level hyperautomation?
On average, a technician needs around 20 minutes to install a device. The costs often exceed the price of the hardware itself. Impress your customers with a setup that is incredibly quick and easy!

KEYNOA – Your Companion for Digital Trust in Industrial Value Creation.
IT security is the requirement. Flexibility, user experience, and scalability are the bonus. With KEYNOA, you choose the right solution.
KEYNOA uses digital identities to provide device manufacturers with secure authentication, encryption and integrity for connected sensors, applications and machines, revolutionizing onboarding.
Robust protection for your devices
Digital identities are the foundation of a secure product lifecycle. KEYNOA supports you every step of the way.
Interoperable value creation
With KEYNOA, you can proactively create a trustworthy and interoperable supply chain for your customers.
Automatic onboarding
KEYNOA makes tedious and costly configurations a thing of the past. Entire device fleets can now be onboarded in just a few clicks.

Great projects are created when there is trust.
We support established companies in implementing IoT projects using digital identities. KEYNOA is the perfect solution if you want to onboard sensors, controllers, machines and systems securely and quickly.
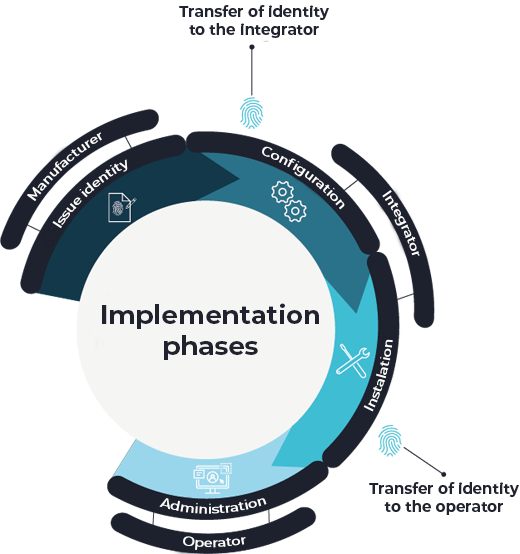
KEYNOA for the entire value chain.

As an integrator, you want to implement the latest technological standards for operators. Recurring tasks should be reliably automated to increase efficiency.
As an operator, you increase your overall equipment effectiveness through the latest automation technology. To ensure plant availability, it is essential to minimize the risk of a cyberattack.
Tailor-made solutions for future-oriented IoT projects and products.
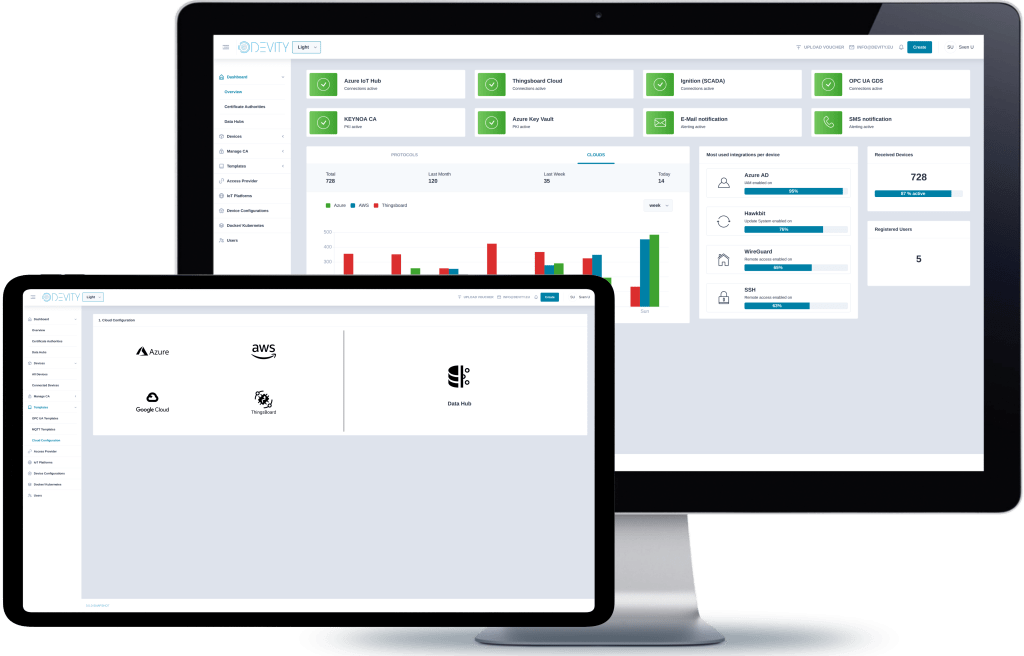
KEYNOA is an orchestration software that serves as a platform and API for managing identities and configurations. Integrators and operators use KEYNOA as a user for onboarding and maintenance. Manufacturers protect their devices with the KEYNOA Engine.

KEYNOA ENGINE
Client for devices for issuing unique identities. Protects the integrity of the device in the supply chain and serves as an initiator for a trustworthy configuration.
ARMv6/ ARMv7/ x86_64
SDK in C
Open standards
KEYNOA
A platform designed for the secure and efficient transfer of trust within the supply chain, as well as the management of device security and configurations.
API first
Docker
SaaS or
On-Premises
On-Premises
The advantages of KEYNOA at a glance.
Time saving
The onobarding costs of industrial components and IoT devices are reduced by up to 90%.
Compliance
With strong device identities, you meet basic requirements for IEC 62443, NIS-2 and the Cyber Resilience Act.
Scalability
The devices can be configured by IT teams anywhere in the world, regardless of location. Whether for 5 or 10,000 devices.
Untrusted Installer
Installers do not need access to sensitive infrastructure to add a device to a network.
Flexibility
Owners can only decide at a very late stage - namely during installation - what the devices are to be used for.
Simplicity
Onboarding processes can be carried out quickly and efficiently by people with any level of experience.
Simple implementation thanks to standardization.
KEYNOA is designed to easily integrate with your existing security infrastructure, including PKI solutions, data platforms and device management systems.
This inspires our customers and partners.
By bundling expertise in the field of hardware and research-related IT security, KEYNOA creates strong synergies for customers in industrial automation.

Ulrich Lütke-Entrup
Key Account Manager, Janz Tec AG
Customer benefit and customer satisfaction are our top priorities. Our claim is the highest quality in technology and service. KEYNOA allows us to focus on exactly that.

Marvin Fortkord
Managing Director, marvIT GmbH
The cooperation between DENIOS and DEVITY is always reliable, characterized by a very high level of technical expertise and an agile, trusting relationship.

Udo Roth
Project Manager Digital Solutions, Denios SE
Project inquiries
info@devity.eu
Telephone
0159 01049052













