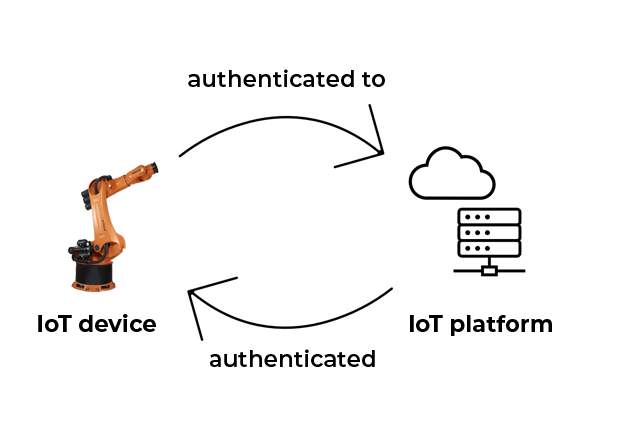Devices can be configured by IT teams worldwide, regardless of location. Connections to IoT clouds like Azure, AWS, or Cumulocity are established using OPC-UA or MQTT protocols.
KEYNOA also supports integration with external PKI systems and device management solutions, ensuring users retain full independence and data sovereignty at all times.