Using identities to scale up your IoT products & projects.
Use digital identities...
Strong device protection as a basis.
KEYNOA was developed to make IT security in the IoT simple and effective. Unique digital identities are a basic requirement for many protection mechanisms. We help manufacturers to use these identities securely and make them available for digital services.
...Along the value chain...
Trust at the heart of the supply chain.
To ensure the integrity of devices in the value chain, it must be guaranteed that only authorized persons can access a device. It is therefore important to clearly transfer ownership of the device. Our innovative technology uses this principle to enable efficient and precise configuration of device fleets.
...to scale the onobarding.
Automatic onboarding as a driver.
Zero-touch is invaluable in industrial IoT projects as it enables fast and automated onboarding of devices without manual intervention on site. This shortens implementation times, reduces sources of error and simplifies the integration of new devices into existing systems.
KEYNOA - How it works!
One process for trust in the entire value chain, many potentials for the entire value chain.
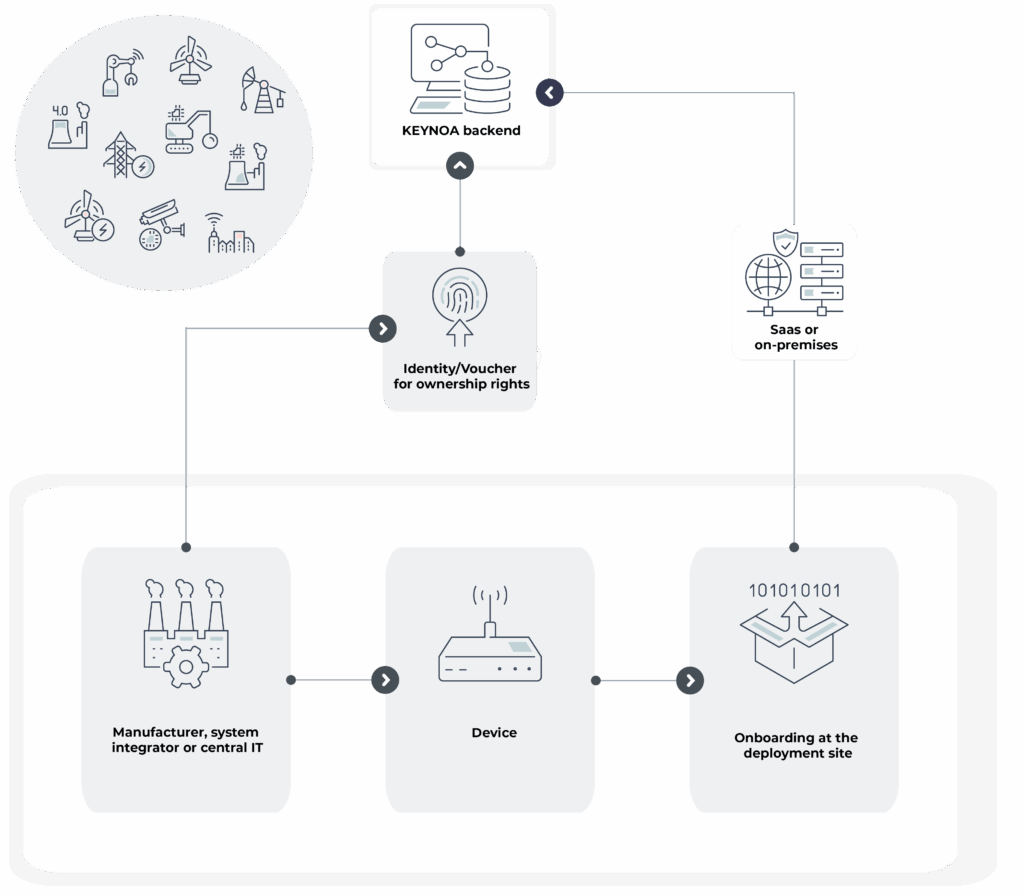
The manufacturer produces a device with a unique identity and creates a proof of ownership.
The manufacturer transfers the proof of ownership using KEYNOA and sends the device to the customer.
The integrator or operator uses the proof of ownership to define central configurations for all devices.
A person who does not have to be trustworthy installs and starts the device.
The device registers its identity with KEYNOA.
KEYNOA authenticates the device and authorizes the exchange of information via a secure channel.
The device downloads secrets and files from KEYNOA and performs an automatic configuration according to the previously defined specifications.
The components of KEYNOA.
One process for trust in the entire value chain, many potentials for the entire value chain.
Engine
- Is installed on the device as a client.
- Can be implemented in firmware or as an operating system process.
- Queries KEYNOA instances to initiate automatic onboarding.
- Compatible with the use of TPM for strong private key protection.
Producer Service
- Is preferably in the production of the device manufacturer.
- Signs the device.
- Creates a certificate that establishes ownership.
- Takes over the assignment to customers.
- Seamless connection to picking systems.
KEYNOA
- Receipt and transfer of the proofs of ownership generated by the Producer Service within the supply chain.
- Can be installed as software on your own servers (on-premises) or in the cloud. As a SaaS solution, DEVITY takes over the hosting completely.
- KEYNOA checks the device identity and provides the device with information about which entities are trustworthy.
- After mutual authentication, a secure channel is set up between the device and this server, via which the data required for onboarding automation (e.g. files and scripts) is sent to the device.
Start quickly - scale flexibly.
We promise you reliability, trust and stability at every stage of our cooperation.
Eval kit
Get to know the advantages of automated onboarding processes. We will provide you with the KEYNOA Engine with a suitable device and our KEYNOA backend free of charge for four weeks – completely risk-free.
Co-innovation
Start the next phase of your IoT project. Together we will improve IT security and efficiency within a few weeks. You receive your own KEYNOA backend and individual consulting and development services.
Integration
KEYNOA can be seamlessly integrated into your system landscape. Benefit from our expertise in the development of sustainable IT security concepts and zero-touch solutions along the value chain.
Get in touch.
Would you like to book a demo or have further questions? Then book a session with our CEO to understand how to make your infrastructures and projects more secure and scalable.
