KEYNOA features
Scalable device networking with KEYNOA.
With KEYNOA, you can connect any device to any data platform in seconds — thousands of times over.
The features of KEYNOA.
Central configuration
Automate device configuration with KEYNOA.
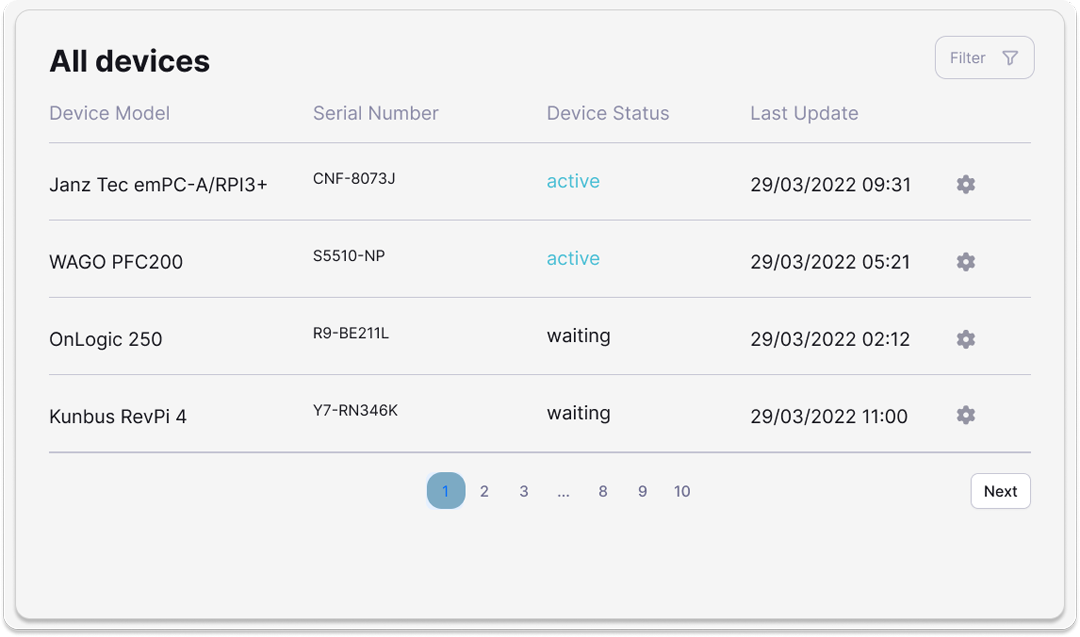
From defining profiles and configuration templates to remote diagnostics, software management, and security, KEYNOA offers centralized control over all devices and device groups.
Centralized configuration and management of all devices and device groups.
Configurations can be modified right up until the point of physical installation.
Service technicians require no access to critical networks.
Diverse integration options
Different devices, varied purposes, and complex infrastructures? No problem with KEYNOA.
KEYNOA integrates seamlessly with existing infrastructures such as IoT clouds, SCADA systems and public key infrastructures, enabling secure, encrypted data exchange with proven protocols.
Compatible with on-premises platforms and major clouds like Azure, AWS, Google Cloud, and ThingsBoard.
Encrypted communication with certificate-based authentication using standardized protocols (e.g., OPC UA, MQTT, HTTPS, BACnet/SEC, and IEC 60870-5-104).
Simple integration and management of existing access to third-party systems.
API-first architecture for flexible and scalable deployment.

Device management
Ensuring the security of devices and data requires robust protection measures against unauthorized access. Authorization should only be granted to individuals and systems that absolutely need it to perform their tasks, and only with the permissions necessary for their work. Permanent authorizations, such as default passwords, should never be used.
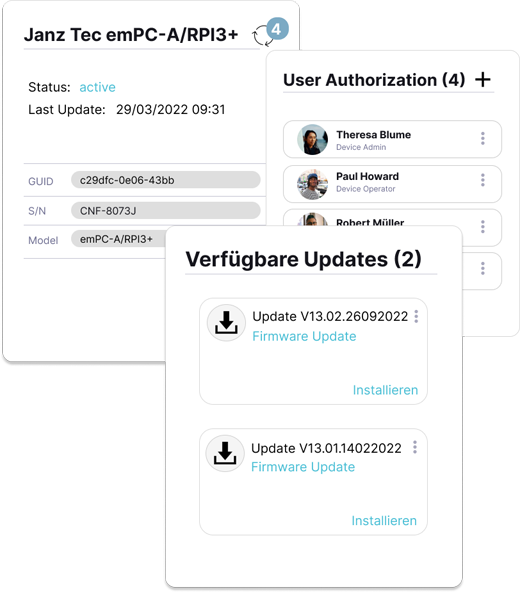
With KEYNOA's identity and access management, you can provide external service technicians with secure access to devices while ensuring that only authorized individuals can use the appropriate tools. This approach helps protect against social engineering attacks and ensures that critical updates are never missed or overlooked.
Manage access to installed devices centrally and enable secure remote access.
Seamlessly integrate with existing IAM systems, such as Microsoft Active Directory (Entra ID).
Manage and automate updates via a central dashboard.
Identity management
KEYNOA employs cutting-edge security mechanisms for the IoT to enhance device security.
At its core are trusted devices and advanced IoT security measures, minimizing vulnerabilities from both external and internal threats.
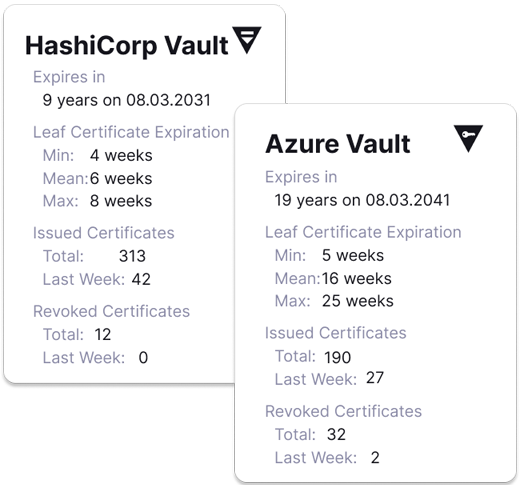
Automatic certificate management.
Secure revocation of device identities.
Mutual authentication of device and data platform.
Automatic onboarding
In automation or IoT projects, deploying hundreds of devices can be time-consuming. Service technicians often spend about 20 minutes per device authenticating, configuring, and installing software. This process must be repeated for every additional device, making it inefficient for large-scale deployments.
Device onboarding in complex and distributed systems goes beyond simple network configuration. With KEYNOA, you can effortlessly automate workflows customized for specific devices, customers, locations, applications, and integrations.
Zero-touch deployment in less than two minutes.
An untrusted installer approach allows installation by individuals without requiring trust credentials.
Mutual authentication aligns with zero trust concepts to enhance security.

Operating
Keep a complete overview of your IoT devices.
KEYNOA enables you to manage devices throughout every phase of their lifecycle. The intuitive KEYNOA dashboards provide a comprehensive view of IoT device metadata, including connection status to IoT clouds, update versions, IT security features, and access authorizations.
Create a single source of truth (SSOT) for your fleet management.
View all connections at a glance.
Monitor devices individually and make flexible adjustments as needed.

Learn how KEYNOA is implemented.
We integrate KEYNOA into any device. Just let us know your requirements.
What makes KEYNOA unique?
Each device is given a unique identity during production.

No-Code Platform for device management and IT security.
