
IT security solutions for small businesses: The CyberRiskCheck
IT security solution for small businesses: The CyberRiskCheck
IT security solutions for small businesses: The CyberRiskCheck

What is the CyberRiskCheck?
Existing IT security standards are largely aimed at large companies. Until now, these standards have been too extensive for small and medium-sized companies.

What are the challenges facing companies in terms of IT security?
Companies face a variety of challenges when it comes to protecting themselves against the increasing threat situation:
Complex IT security
Limited budget
Shortage of time
Why is the CyberRiskCheck relevant for companies?
How does the CyberRiskCheck work?
1st evaluation meeting
In the first step, an initial meeting is held to collect initial company data, which is later evaluated in the results report. In addition, the company to be advised is informed which documents (emergency plans, backup concepts, access concepts, etc.) need to be prepared. Furthermore, the responsible persons who are to participate in the consulting process are determined.
2. cyber risk check
3. evaluation of the data
4. presentation of the results
The cyber risk check and the results report it contains serve as the basis for further steps. For example, companies can be commissioned to implement the recommendations for action.
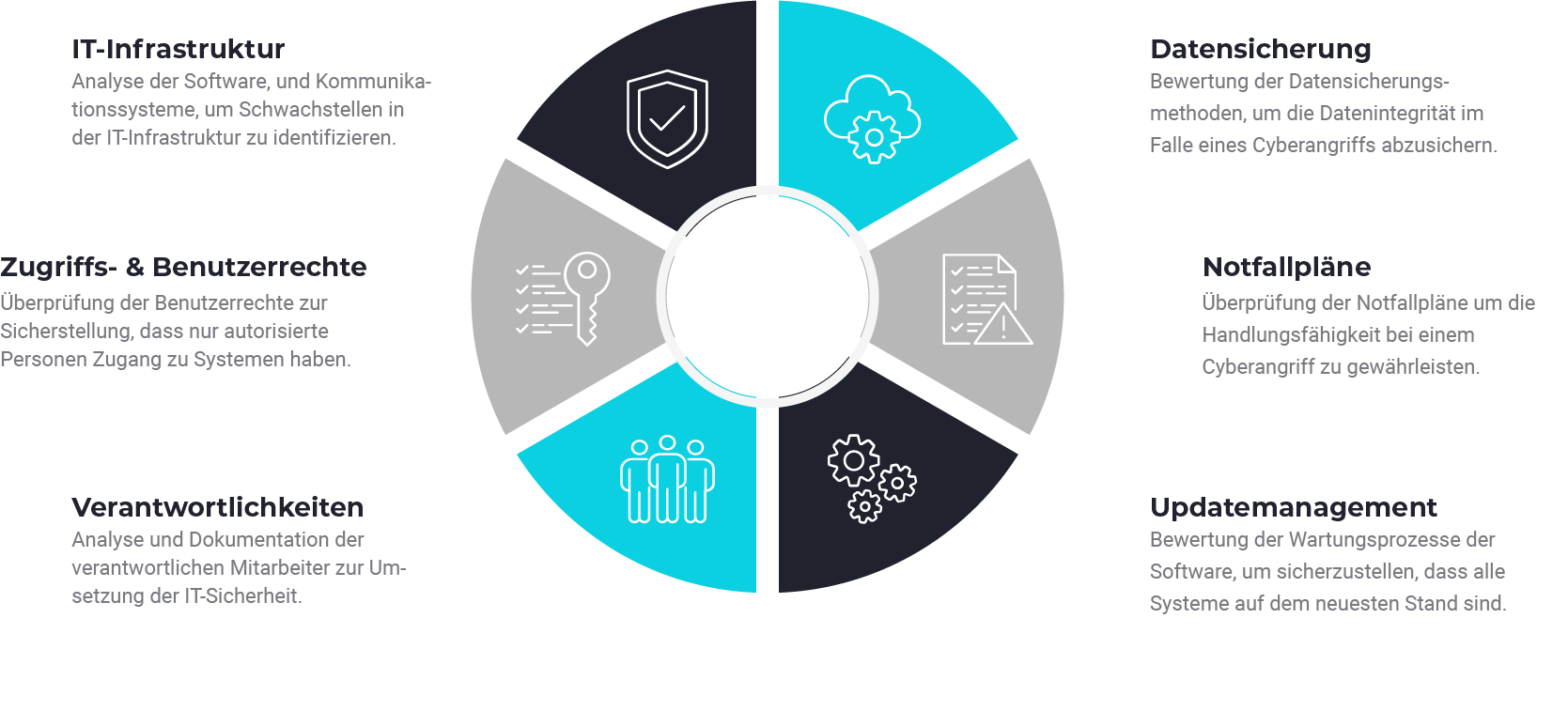
What is checked during the CyberRiskCheck?
What are the benefits of the CyberRiskCheck?
Quick start
The CyberRiskCheck offers companies a simple introduction to information security. In just four uncomplicated steps, companies receive a sound and comprehensible analysis of their current IT security situation and potential risks.
Clear test criteria
The CyberRiskCheck contains 27 requirements, which are divided into regular and important requirements. This makes it clear to the company which measures should be prioritized in order to reduce acute threats.
Customized results report
The IT service provider evaluates the collected data and creates a customized results report. This report provides the individual risk status value, a visualization of the weak points and an overview of relevant recommendations for action.
Practice-oriented recommendations
The recommendations for action are specific and sorted by urgency and contain concrete measures to eliminate identified security gaps. This gives companies the opportunity to improve potential weaknesses in information security in a targeted manner.