Use for device manufacturers
Interoperable devices for the networking of the future.

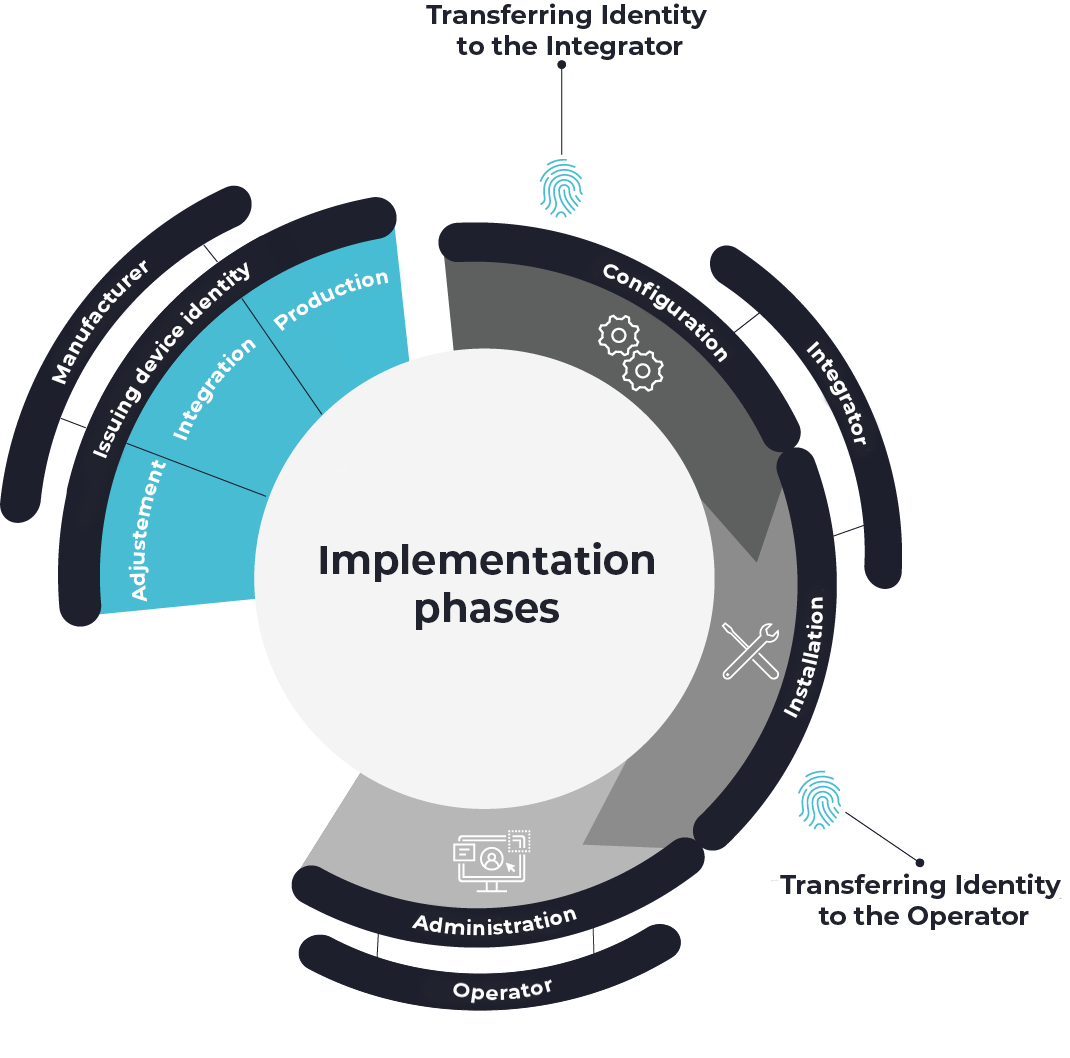
Steps for implementing KEYNOA.
1. Adjustment
In the first step, our embedded team checks compatibility with the existing device software. Thanks to its flexible structure and support for common standards, the KEYNOA Engine guarantees simple adaptation and interoperability.
2. Integration
In the second step, we integrate the KEYNOA engine and demonstrate how it interacts with your device. If you already have a Trusted Platform Module (TPM), we will show you how cryptographic keys and certificates are securely stored and managed.
3. Production
During production, a unique, cryptographically bound identity is created for each device, which can be uniquely assigned to the device. This identity ensures the integrity of the device within the supply chain and forms the basis for the automatic onboarding process. DEVITY provides the Producer Service for this purpose.
The components of KEYNOA.
Engine
- Is installed on the device as a client.
- Can be implemented in firmware or as an operating system process.
- Queries KEYNOA instances to start automatic onboarding.
- Compatible for the use of TPM for strong protection of the private key.
Producer Service
- Is preferably in the production of the device manufacturer.
- Signs the device securely and automatically.
- Creates proof that clearly confirms ownership of the device.
- Takes over the assignment to customers.
- Seamless integration into order picking systems.
KEYNOA
- Receipt and transmission of the proof of ownership generated by the Producer Service along the supply chain.
- Can be installed both on your own servers (on-premises) and in the cloud. With the SaaS solution, DEVITY takes over the complete hosting.
- KEYNOA verifies the device identity and provides the device with information about trusted entities.
- After mutual authentication, a secure channel is set up between the device and the server via which the data required for onboarding automation (e.g. files and scripts) is transferred to the device.
Your added value with KEYNOA.
Use and benefit from KEYNOA to the full. You can realize the following advantages by using KEYNOA:
Onboarding
Instant onboarding of thousands of devices.
Cost-efficient
Optimization of operating and maintenance costs.
IT security
Protection of integrity and confidentiality over the entire life cycle.
KEYNOA in use.

Initial situation
Numerous manual steps are required to install sensors in large-scale systems.
The customer, a sensor manufacturer, aims to enhance the functionality of its devices by centralizing configuration and securely integrating current industry protocols. Previously, onboarding hundreds of sensors into customers' systems involved many manual steps.
Solution
IT security for intelligent sensors.
In production, each sensor is given a unique, cryptographically secured identity that can be clearly assigned to the device. The device identities are transferred directly to the customer via the Producer Service so that the IT administrator can start configuring the sensors before physical delivery.
As all the systems are connected to the cloud, the operator uses the KEYNOA platform as a browser-based SaaS solution. This allowed the devices to be supplied with the information and configurations required for operation directly via the previously issued identity - without unpacking.
Result
An efficient and networked system.
With KEYNOA, thousands of IoT sensors can be networked across locations and configured in no time at all, without the need for IT specialists on site. Thanks to the fast setup and integration of systems, the sensor manufacturer can use IoT networking immediately. KEYNOA also supports the company with complete device management over the entire lifecycle, so that no more updates or security patches are missed.

